Many Telekom customers in Germany had to live without internet and telephone on the weekend. Hackers tried to install malware on 900,000 routers and integrate them into a botnet. Presumably to carry out DDoS-attacks. Fortunately, this did not work out thanks to a badly programmed software. However, DDoS-attacks with web-enabled devices have already caused great sensation in 2016. Foremost the attack on the DNS-provider DYN in October this year.
We wanted to know, how DDoS-attacks work, which aims the offenders have and which precaution measures against the attacks are useful.
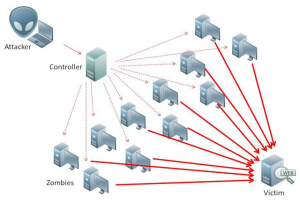
Procedure at DDos-attacks
DDoS is the abbreviation for “Distributed Denial of Service”. Thus, when a DDoS-attack happens, it should suspend the availability of a computer or system.
The victim’s system is bombarded with such a high number of service data which cannot be processed anymore. As a result, regular requests by users can only be answered slowly or not at all.
The attack occurs with many spread out computers, or rather devices which are infected with malware – a so-called botnet. That is how third parties can control the devices without the owner knowing of it.
Aims of the offenders
DDos-attacks are one of the most common cyber attacks today. Aim of the attacks are foremost companies based in the industrial or financial sector. The company is supposed to be put under pressure. However, DDoS-attacks can also be a form of protest. Besides, now they are also used in cyber espionage.
Networked devices with an independent existence
The increasing meaning of the internet of things leads to smart devices being abused for DDoS-attacks. Hence all web-enabled devices can become potential tools of cyber criminals. Since they are often delivered with standard passwords and companies rarely update, they are easily to manipulate. Many users do not change their password after they connected their device. This makes it especially easy for hackers to abuse the devices to create a botnet.
Producers are criticized
Not only user are criticized but also the device producers are responsible according to experts. Manufactures rarely publicize updates for their produced devices. The smart devices are so quickly developed that it is not worthwhile to bring updates for old models. Furthermore, producers have to communicate better with their customers. A certain number of users does not know that their device needs regular updates. In addition, producers could force customers to change their password with a software.
Attack on Dyn: Twitter, Amazon and Netflix were not available
In the morning of October 21 2016, many people on the east coast of the United States had to live for hours without Twitter, Netflix and Spotify. The internet service provider Dyn was the victim of a DDoS-attack. The attack used digital cameras which were infected with the malware Mirai. Although the DNS-provider Dyn protects itself against such attacks, it could not hold out the surge. As a result, also websites of Dyn customers were not available. Besides, the created botnet by Mirai has capacity of one terabit and it therefore the biggest known net of this kind.
DDoS-attack against journalist Brian Krebs: using a sledgehammer to crack a nut
The website of journalist Brian Krebs was also recently affected by a massive DDoS-attack. During the attack, 620 gigabit per second were send to Krebs website and thereby shut it down. Usually a fraction of this data volume is sufficient to bring a website to standstill. Moreover, the attacks against Krebs and Dyn probably had the same origin. In the case of Krebs website, the attack could also be attributed to “Mirai”.
Protection against DDoS-attacks at POLYAS
It is complicated to protect yourself preventative against DDoS-attacks, but measures can be taken to moderate the consequences of an attack. We at POLYAS work with trustworthy service provider.
Furthermore, our infrastructure is constructed in a way which does not allow a Single Point auf Failure. This means that our servers are at various locations and the incoming and outgoing data do not converge at one point. So if one server breaks down, a complete breakdown of the system can be avoided. By using this smart system, we can guarantee a high server availability and security of our customer’s data.
In case of a DDoS-attack, we outsource the affected parts of our infrastructre to different cloud servers until the surge is over. In additon, we work with several server providern to have a permanent alternative solution at hand.